GOOD NEWS: All the new added 70-410 exam questions and answers can get in VCE and PDF format for free on Lead2pass. With Lead2Pass 70-410 practice tests, you will pass the exam easily! Free download 70-410 445q exam questions vce player all the time.
QUESTION 81
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains a server named Server1 that runs Windows Server 2012 R2.
You need to ensure that when users log on to Server1, their user account is added automatically to a local group named Group1 during the log on process.
Which Group Policy settings should you modify?
A. Restricted Groups
B. Security Options
C. User Rights Assignment
D. Preferences
Answer: D
Explanation:
A. If a Restricted Groups policy is defined and Group Policy is refreshed, any current member not on the Restricted Groups policy members list is removed
B. Security settings incorporated into policies are rules that administrators configure on a computer or multiple computers for the purpose of protecting resources on a computer
C. User Rights Assignment policies determines which users or groups have logon rights or privileges on the computer
D. With Preferences, local and domain accounts can be added to a local group without affecting the existing members of the group
http://technet.microsoft.com/en-us/library/cc785631(v=ws.10).aspx
http://www.grouppolicy.biz/2010/01/how-to-use-group-policy-preferences-to-secure-localadministrator-groups/
http://technet.microsoft.com/en-us/library/cc780182(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh831424.aspx
QUESTION 82
Your network contains an Active Directory domain named contoso.com.
You need to prevent users from installing a Windows Store app named App1.
What should you create?
A. An application control policy executable rule
B. An application control policy packaged app rule
C. A software restriction policy certificate rule
D. An application control policy Windows Installer rule
Answer: B
Explanation:
Windows 8 is coming REALLY SOON and of course one of the big new things to computer with that is the newPackaged Apps that run in the start screen. However these apps are very different and do not install liketraditional apps to a path or have a true “executable” file to launch the program. Ofcourse enterprises need a way to control these packaged apps and therefore Microsoft has added a newfeature Packaged Apps option to the App1ocker feature.
A. For .exe or .com
B. A publisher rule for a Packaged app is based on publisher, name and version
C. You can create a certificate rule that identifies software and then allows or does not allow the software torun, depending on the security level.
D. For .msi or .msp
Packaged apps (also known as Windows 8 apps) are new to Windows Server 2012 R2 and Windows 8. They are based on the new app model that ensures that all the files within an app package share the sameidentity.
Therefore, it is possible to control the entire Application using a single App1ocker rule as opposed to the nonpackagedapps where each file within the app could have a unique identity. Windows does not support unsigned packaged apps which implies all packaged apps must be signed. App1ocker supports only publisher rules for Packaged apps. A publisher rule for a Packaged app is based on the following information:
Publisher of the package
Package name
Package version
Therefore, an App1ocker rule for a Packaged app controls both the installation as well as the running of theapp. Otherwise, the publisher rules for Packaged apps are no different than the rest of the rule collections; theysupport exceptions, can be increased or decreased in scope, and can be assigned to users and groups.
http://technet.microsoft.com/en-us/library/dd759068.aspx
http://technet.microsoft.com/en-us/library/hh994588.aspx
http://www.grouppolicy.biz/2012/08/how-manage-published-a-k-a-metro-apps-in-windows8-using-grouppolicy/
http://technet.microsoft.com/en-us/library/hh994597.aspx#BKMK_Cert_RulesPackaged
Apps run in the start screen.
However these apps are very different and do not install like traditional apps to a path or have a true”executable” file to launch the program.
Enterprises need a way to control these packaged apps and therefore Microsoft has added a new featurePackaged Apps option to the App1ocker feature.
QUESTION 83
Your company’s security policy states that all of the servers deployed to a branch office must not have the graphical user interface (GUI) installed. In a branch office, a support technician installs a server with a GUI installation of Windows Server 2012 on a new server, and then configures the server as a DHCP server.
You need to ensure that the new server meets the security policy.
You want to achieve this goal by using the minimum amount of Administrative effort.
What should you do?
A. Reinstall Windows Server 2012 on the server.
B. From Windows PowerShell, run Uninstall-WindowsFeature Desktop-Experience.
C. From Windows PowerShell, run Uninstall-WindowsFeature PowerShell-ISE.
D. From Server Manager, uninstall the User Interfaces and Infrastructure feature.
Answer: D
Explanation:
A. Not least effort
B. Uninstalls desktop experience not the full GUI
C. Uninstalls the powershell ISE
D. Least effort and removes full GUI
http://www.howtogeek.com/111967/how-to-turn-the-gui-off-and-on-in-windows-server-2012/
http://technet.microsoft.com/en-us/library/cc772567.aspx http://blogs.technet.com/b/server_core/archive/2012/05/09/configuring-the-minimal-serverinterface.aspx
QUESTION 84
Your network contains an Active Directory domain named contoso.com. The domain contains 500 servers that run Windows Server 2012 R2.
You have a written security policy that states the following:
– Only required ports must be open on the servers.
– All of the servers must have Windows Firewall enabled.
– Client computers used by Administrators must be allowed to access all of the ports on all of the servers.
– Client computers used by the Administrators must be authenticated before the client computers can access the servers.
You have a client computer named Computer1 that runs Windows 8.
You need to ensure that you can use Computer1 to access all of the ports on all of the servers successfully. The solution must adhere to the security policy.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. On Computer1, create a connection security rule
B. On all of the servers, create an outbound rule and select the Allow the connection if it is secureoption.
C. On all of the servers, create an inbound rule and select the Allow the connection if it is secureoption.
D. On Computer1, create an inbound rule and select the Allow the connection if it is secureoption.
E. On Computer1, create an outbound rule and select the Allow the connection if it is secureoption
F. On all of the servers, create a connection security rule
Answer: ACF
Explanation:
http://technet.microsoft.com/en-us/library/cc772017.aspx
Unlike firewall rules, which operate unilaterally, connection security rules require that both communicating computers have a policy with connection security rules or another compatible IPsec policy.
http://technet.microsoft.com/en-us/library/cc753463.aspx
Traffic that matches a firewall rule that uses the Allow connection if it is secure setting bypasses Windows Firewall. The rule can filter the traffic by IP address, port, or protocol. This method is supported on Windows Vista or Windows Server 2008.
QUESTION 85
Drag and Drop Question
Your network contains three servers. The servers are configured as shown in the following table.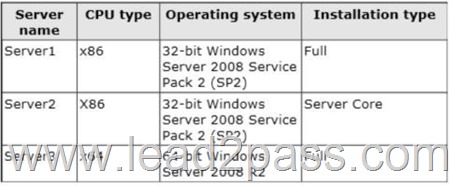
Your company plans to standardize all of the servers on Windows Server 2012 R2.
You need to recommend an upgrade path for each server.
The solution must meet the following requirements:
– Upgrade the existing operating system whenever possible.
– Minimize hardware purchases.
Which upgrade path should you recommend for each server? To answer, drag the appropriate upgrade path to each server in the answer area. Each upgrade path may be used once, more than once, or not at all.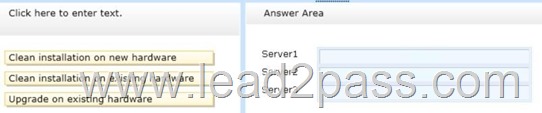
Answer: 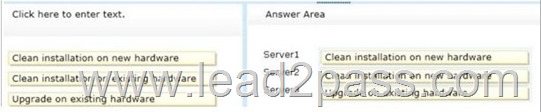
Explanation:
Server1 not 64-bit processor
Server2 not 64-bit processor
Server3 64-bit processor, needs 2008 SP1
http://blogs.technet.com/b/askcore/archive/2012/10/23/upgrading-to-windows-server-2012-part-1.aspx
http://technet.microsoft.com/en-us/library/jj134246.aspx
QUESTION 86
Your network contains a file server named Server1 that runs Windows Server 2012 R2. All client computers run Windows 8. Server1 contains a folder named Folder1. Folder1 contains the installation files for the company’s desktop applications.
A network technician shares Folder1 as Share 1.
You need to ensure that the share for Folder1 is not visible when users browse the network.
What should you do?
A. From the properties of Folder1, deny the List Folder Contents permission for the Everyone group.
B. From the properties of Folder1, remove Share1, and then share Folder1 as Share1$.
C. From the properties of Folder1, configure the hidden attribute.
D. From the properties of Share1, configure access-based enumeration
Answer: B
Explanation:
A. Will deny everyone list of folder content
B. Remove share and re-add using $ for Hidden/Administrative share
C. This will hide the physical folder
D. lists only the files and folders to which they have access when browsing content on the file server A hidden share is identified by a dollar sign ($) at the end of the share name
Hidden shares are not listed when you look through the shares on a computer or use the “net view” command
Why Use Hidden Shares?
Using hidden shares on your network is useful if you do not want a shared folder or drive on the network to beeasily accessible. Hidden shares can add another layer of protection for shared files against unauthorizedpeople connecting to your network. Using hidden shares helps eliminate the chance for people to guess yourpassword (or be logged into an authorized Windows account) and then receive access to the shared resource.
http://support.microsoft.com/kb/314984
http://technet.microsoft.com/en-us/library/cc784710(v=ws.10).aspx
QUESTION 87
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and a server named Server2 that runs Windows Server 2008 R2 Service Pack 1 (SP1). Both servers are member servers. On Server2, you install all of the software required to ensure that Server2 can be managed remotely from Server Manager.
You need to ensure that you can manage Server2 from Server1 by using Server Manager.
Which two tasks should you perform on Server2? (Each correct answer presents part of the solution. Choose two.)
A. Run the systempropertiesremote.execommand
B. Run the Enable-PsRemotingcmdlet.
C. Run the Enable-PsSessionConfigurationcmdlet
D. Run the Confiqure-SMRemoting.ps1script
E. Run the Set-ExecutionPolicycmdlet.
Answer: DE
Explanation:
To configure Server Manager remote management by using Windows PowerShell On the computer that you want to manage remotely, open a Windows PowerShell session with elevated user rights. To do this, click Start, click All Programs, click Accessories, click Windows PowerShell, right-click the Windows PowerShell shortcut, and then click Run as administrator. In the Windows PowerShell session, type the following, and then press Enter.
Set-ExecutionPolicy -ExecutionPolicyRemoteSigned
Type the following, and then press Enter to enable all required firewall rule exceptions.
Configure-SMRemoting.ps1 -force -enable
http://technet.microsoft.com/en-us/library/dd759202.aspx
A) Run the systempropertiesremote.exe command
B) Enable-PSRemotingcmdlet configures the computer to receive Windows PowerShell remote commandsthat are sent by using the WS-Management technology.
C) Enable-PSSessionConfigurationcmdlet enables registered session configurations that have been disabled.
D) Configure-SMRemoting.ps1 -force -enable
E) Set-ExecutionPolicy -ExecutionPolicyRemoteSigned
To configure Server Manager remote management by using Windows PowerShell On the computer that you want to manage remotely, open a Windows PowerShell session with elevated userrights, type the following:
To configure Server Manager remote management by using Windows PowerShell. On the computer that youwant to manage remotely, open a Windows PowerShell session with elevated user rights. To do this, click Start, click All Programs, click Accessories, click Windows PowerShell, right-click the WindowsPowerShell shortcut, and then click Run as administrator. In the Windows PowerShell session, type thefollowing, and then press Enter. Set-ExecutionPolicy –
ExecutionPolicyRemoteSigned Type the following, and then press Enter to enable allrequired firewall rule exceptions.
Configure-SMRemoting.ps1 -force -enable
http://technet.microsoft.com/en-us/library/dd759202.aspx
QUESTION 88
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains a print server named Server1 that runs Windows Server 2012 R2.
You share several printers on Server1.
You need to ensure that you can view the printer objects associated to Server1 in Active Directory Users and Computers.
Which option should you select? To answer, select the appropriate option in the answer area.
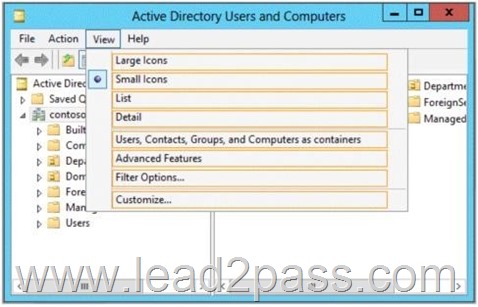
Answer: 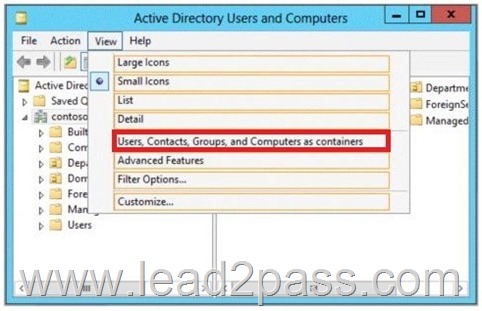
Explanation:
You can view printer objects in Active Directory by clicking Users, Groups, and Computers as containers from the View menu in the Active Directory Users and Computers snap-in.
By default, printer objects are created under the machine object in which they are shared. After you turn on the Users, Groups, and Computers as containers option, you can see printers by expanding the printer’s host computer.
http://support.microsoft.com/kb/235925
QUESTION 89
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2 that run Windows Server 2012 R2.
You log on to Server1.
You need to retrieve the IP configurations of Server2.
Which command should you run from Server1?
A. winrs -r:server2 ipconfig
B. winrm get server2
C. dsquery *-scope base-attr ip, server2
D. ipconfig > server2.ip
Answer: A
Explanation:
A. Windows Remote Management allows you to manage and execute programs remotely
B. winrm is the server side services for remote mgmt
C. dsquery * finds any objects in the directory according to criteria using a LDAP query.
D. Would output server1 ipconfig info to server2.ip file
http://technet.microsoft.com/en-us/library/dd349801(v=ws.10).aspx
QUESTION 90
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2008 R2 installed. Some of L2P.com’s workstations have Windows 7 installed, while the rest have Windows 8 installed.
After installing a new Windows Server 2012 computer in the L2P.com domain, you configure it to run the File and Storage Services server role. You are instructed to create a shared folder on the new server, and configure the use of Previous Versions for restoring files located in the shared folder.
Which of the following actions should you take?
A. You should consider configuring the Shadow Copies settings on the new server.
B. You should consider configuring the Snapshot settings on the new server.
C. You should consider configuring the Background Copy settings on the new server.
D. You should consider configuring the Permission settings on the new server.
Answer: A
Explanation:
What are previous versions?
Previous versions are either backup copies (copies of files and folders that you back up by using the Back Up Files wizard, or shadow copies) copies of files and folders that Windows automatically saves as part of a restore point. (Shadow copies can be copies of files on your computer or shared files on acomputer on a network.) You can use previous versions of files to restore files that you accidentally modified or deleted, or that were damaged. Depending on the type of file or folder, you can open, save to a different location, or restore a previous version.
ATT: ( nothing to do with question but cool to know ) File Server Volume Copy Shadow Service (VSS) Agent Service Enables consistency of application snaphots (shadow copies). With previous versions of Windows Server, VSS only supported shadow copies of data on the local server. With WS2012, Microsoft has added VSS for SMB File Shares which extends shadow copy support for network volumes.Administrators install the FS VSS Agent on the file server where the application data is located. They then install the VSS provider in the server where the application is located. The provider talks to the agent using the new File Server Remote VSS protocol in order to manage the shadow copies of the data.
http://windows.microsoft.com/en-gb/windows-vista/previous-versions-of-files-frequently-asked-questions
QUESTION 91
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. The disks on Server1 are configured as shown in the exhibit. (Click the Exhibit button.)
You create a virtual machine on Server1.
You need to ensure that you can configure a pass-through disk for the virtual machine.
What should you do?
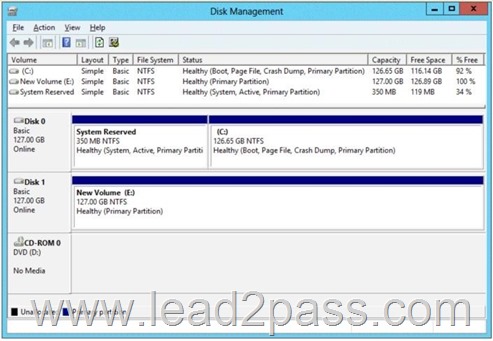
A. Delete partition E.
B. Convert Disk 1 to a GPT disk
C. Convert Disk 1 to a dynamic disk.
D. Take Disk 1 offline.
Answer: D
Explanation:
Pass-Through Disk must be offline
Pass-through Disk Configuration
Hyper-V allows virtual machines to access storage mapped directly to the Hyper-V server without requiring thevolume be configured. The storage can either be a physical disk internal to the Hyper-V server or it can be aStorage Area Network (SAN) Logical Unit (LUN) mapped to the Hyper-V server. To ensure the Guest hasexclusive access to the storage, it must be placed in an Offline state from the Hyper-V serverperspective
http://blogs.technet.com/b/askcore/archive/2008/10/24/configuring-pass-through-disks-inhyper-v.aspx
http://technet.microsoft.com/pt-pt/library/ff404147%28v=ws.10%29.aspx
QUESTION 92
Your network contains an Active Directory domain named contoso.com.
The domain contains two servers named Server2 runs Windows Server 2012 R2.
You create a security template named Template 1 by using the Security Templates snap-in.
You need to apply template 1 to Server 2.
Which tool should you use?
A. Security Templates.
B. Computer Management.
C. Security Configuration and Analysis.
D. System Configuration.
Answer: C
Explanation:
Security templates are inactive until imported into a Group Policy object or the Security Configurationand Analysis.
http://technet.microsoft.com/en-us/library/jj730960.aspx
http://windows.microsoft.com/en-us/windows-vista/using-system-configuration
QUESTION 93
Your network contains an active directory domain named contoso.com. The domain contains a domain controller named DC5. DC5 has a server core installation of Windows Server 2012 R2.
You need to uninstall Active Directory from DC5 manually.
Which tool should you use?
A. The Remove-WindowsFeature cmdlet
B. the dsamain.exe command
C. the ntdsutil.exe command
D. the Remove-ADComputer cmdlet
Answer: C
Explanation:
A. Removes Roles and Features to remove DC use Uninstall-addsdomaincontroller
B. Exposes Active Directory data that is stored in a snapshot or backup as a Lightweight Directory Access
Protocol (LDAP) server
C. Manually removes a domain controller
D. Removes AD computer object
Ntdsutil.exe is a command-line tool that provides management facilities for Active Directory Domain Services (AD DS) and Active Directory Lightweight Directory Services (AD LDS).
You can use the ntdsutil commands to perform database maintenance of AD DS, manage and control single master operations, and remove metadata left behind by domain controllers that were removed from the network without being properly uninstalled.
This tool is intended for use by experienced administrators.
http://technet.microsoft.com/en-us/library/ee662310.aspx
http://support.microsoft.com/kb/216498
http://technet.microsoft.com/en-us/library/ee617250.aspx
QUESTION 94
You have a server named Server 2 that runs Windows Server 2012 R2. Server 2 has the Hyper-V server role installed.
The disks on Server2 are configured as shown in the exhibit. (Click the Exhibit button).
You create a virtual machine on Server2 named VM1.
You need to ensure that you can configure a pass-through disk for VM1. What should you do?
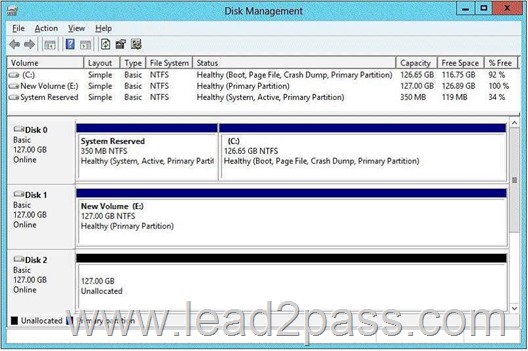
A. Convert Disk 1 to a MBR disk.
B. Convert Disk 1 to a basic disk.
C. Take Disk 1 offline.
D. Create a partition on Disk 1.
Answer: C
Explanation:
Pass-through Disk Configuration
Hyper-V allows virtual machines to access storage mapped directly to the Hyper-V server without requiring the volume be configured. The storage can either be a physical disk internal to the Hyper-V server or it can be a Storage Area Network (SAN) Logical Unit (LUN) mapped to the Hyper-V server. To ensure the Guest has exclusive access to the storage, it must be placed in an Offline state from the Hyper-V server perspective
http://blogs.technet.com/b/askcore/archive/2008/10/24/configuring-pass-through-disks-in-hyper-v.aspx
QUESTION 95
You have a file server named Server1 that runs Windows Server 2012 R2.
Server1 has following hardware configurations:
– 16GB of RAM
– A single quad-core CPU
– Three network teams that have two network adapters each
You add additional CPUs and RAM to Server 1.
You repurpose Server1 as a virtualization host.
You install the Hyper-V server role on Server1. You need to create four external virtual switches in Hyper-V.
Which cmdlet should you run first?
A. Set-NetAdapter.
B. Add-Net1.bfoTeamNic
C. Add-VMNetworkAdapter
D. Remove-NetLbfoTeam
Answer: D
Explanation:
A. Sets adapter properties
B. Add new interface to NIC Team
C. Adds vadapter to vm
D. Removed NIC from host
You need 4 virtual switches but currently only have 3 teams available.
You would need to break a team first.
http://technet.microsoft.com/en-us/library/jj130875(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj130850(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/hh848564(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj130848(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj130848.aspx
QUESTION 96
Your network contains an Active Directory domain named contoso.com.
The domain contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
You create a security template named Template1 by using the Security Templates snap-in.
You need to apply Template1 to Server2.
Which tool should you use?
A. Authorization Manager
B. Local Security Policy
C. Certificate Templates
D. System Configuration
Answer: B
Explanation:
A security policy is a combination of security settings that affect the security on a computer.
You can use your local security policy to edit account policies and local policies on your local computer.
QUESTION 97
Your network contains an Active Directory domain named adatum.com. The domain contains a member server named Server1 and a domain controller named DC2. All servers run Windows Server 2012 R2. On DC2, you open Server Manager and you add Server1 as another server to manage. From Server Manager on DC2, you right-click Server1 as shown in the exhibit.
You need to ensure that when you right-click Server1, you see the option to run the DHCP console.
What should you do?
A. On Server1, install the Feature Administration Tools.
B. In the domain, add DC1 to the DHCP Administrators group.
C. On DC2 and Server1, run winrm quickconfig.
D. On DC2, install the Role Administration Tools.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/hh831825.aspx
QUESTION 98
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server 2012.
You create a group Manged Service Account named gservice1.
You need to configure a service named Service1 to run as the gservice1 account.
How should you configure Service1?
A. From a command prompt, run sc.exe and specify the config parameter.
B. From Windows PowerShell,run Set-Service and specify the -PassThrough parameter
C. From Windows PowerShell,run Set-Service and specify the -StartupType parameter
D. From Services Console configure the General settings
Answer: A
QUESTION 99
Your network contains an Active Directory domain named contoso.com. An organizational unit (OU) named OU1 contains user accounts and computer accounts. A Group Policy object (GPO) named GP1 is linked to the domain. GP1 contains Computer Configuration settings and User Configuration settings.
You need to prevent the User Configuration settings in GP1 from being applied to users.
The solution must ensure that the Computer Configuration settings in GP1 are applied to all client computers.
What should you configure?
A. the Group Policy loopback processing mode
B. the Block Inheritance feature
C. the Enforced setting
D. the GPO Status
Answer: A
Explanation:
A. Group Policy loopback with replace option needs to be used
B. Blocking inheritance prevents Group Policy objects (GPOs) that are linked to higher sites, domains, ororganizational units from being automatically inherited by the child-level
C. Enforced prevent blocking at lower level
D. The GPO Status. This indicates whether either the user configuration or computer configuration of the GPOis enabled or disabled.
You can use the Group Policy loopback feature to Apply Group Policy Objects (GPOs) that depend only onwhich computer the user logs on to.
User Group Policy loopback processing can be enabled in one of two modes: merge or replace. In mergemode, both GPOs Applying to the user account and GPOs Applying to the computer account are processedwhen a user logs in. GPOs that Apply to the computer account are processed second and therefore takeprecedence – if a setting is defined in both the GPO(s) Applying to the user account, and the GPO(s) Applyingto the computer account, the setting in the GPO(s) Applying to the computer account will be enforced. With thereplace mode, GPOs Applying to the user account are not processed only the GPOs Applying to thecomputer account are Applied. Loopback can be set to Not Configured, Enabled, or Disabled. In the Enabled state, loopback can be set toMerge or Replace. In either case the user only receives user-related policy settings. Loopback with Replace–In the case of Loopback with Replace, the GPO list for the user is replaced in itsentirety by the GPO list that is already obtained for the computer at computer startup (during step 2 in GroupPolicy processing and precedence). The User Configuration settings from this list are Applied to the user.
Loopback with Merge–In the case of Loopback with Merge, the Group Policy object list is a concatenation.
The default list of GPOs for the user object is obtained, as normal, but then the list of GPOs for the computer(obtained during computer startup) is appended to this list. Because the computer’s GPOs are processed afterthe user’s GPOs, they have precedence if any of the settings conflict. This is a COMPUTER setting, which is found under Computer Configuration | Administrative Templates |
System | Group Policy | User Group Policy Loopback Processing Mode You want to create a new OU in AD that is dedicated to computer accounts that will have loopbackprocessing enabled. Create a new GPO in your new OU to enable User Group Policy Loopback Processing and set theappropriate mode (merge / replace).
You will define the user settings you want to Apply to the loopback-enabled PCs via GPOs in this same newOU.
You can define these settings either in the same GPO where you enabled the User Group PolicyLoopback Processing setting, or you create another new GPO in the same OU for your user settings.
Remember that when using the REPLACE mode, none of your other user GPOs will be Applied whena user logs in to a machine that has loopback processing enabled.
ONLY the user settings that aredefined in the GPOs that Apply to that machine will be Applied.
http://msmvps.com/blogs/cgross/archive/2009/10/12/group-policy-loopbackprocessing.aspx
http://technet.microsoft.com/en-us/library/cc782810(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc731076.aspx
http://technet.microsoft.com/en-us/library/cc753909.aspx
http://technet.microsoft.com/en-us/library/cc778238%28v=ws.10%29.aspx
http://technet.microsoft.com/en-us/magazine/dd673616.aspx
QUESTION 100
Your network contains two Hyper-V hosts named Host1 and Host2. Host1 contains a virtual machine named VM1.
Host2 contains a virtual machine named VM2. VM1 and VM2 run Windows Server 2012 R2.
You install the Network Load Balancing feature on VM1 and VM2.
You need to ensure that the virtual machines are configured to support Network Load Balancing (NLB).
Which virtual machine settings should you configure on VM1 and VM2?
A. Router guard
B. DHCP guard
C. Port mirroring
D. MAC address
Answer: D
Explanation:
In Hyper-V, the VM host prevents dynamic MAC address updates as an extra layer of security in thedatacenter. This is because the VM may have full administrator rights, yet it may be untrusted in thedatacenter, for example when the VM hosting is provided by an independent hosting company. In this scenario,we need to make sure that one VM cannot cause a DOS or information disclosure attack against another VM. If a VM is able to spoof its MAC address, then it can spoof the MAC addresses of other VMs and impactother VMs on that host. The physical switches have similar protections and it is up to the admin to enable thatprotection or not. If you do not enable spoofing of MAC address prior to configuring NLB on the VM you could potentially haveproblems with the NLB cluster.
When configuring NLB in unicast mode on Hyper-V with enable spoofing of MAC Address disabled you maysee some of the following symptoms:
When initially configuring NLB you will lose network connectivity on the network adaptor NLB was configuredon.
There will be an NLB error event in the Windows Event Log stating that the network adaptor does not supportdynamic MAC address updates.
After rebooting the server, NLB will appear to be bound to the network adapter, but the cluster VIP will nothave been added to the network adaptor.
The cluster MAC address will still be the original MAC address associated with the network adaptor prior toconfiguring NLB. Use CMD>ipconfig /all to view the MAC address.
It should start with “02-BF-***”
If you ignore all previous symptoms and manually add the VIP you could get an IP conflict if there are othernodes in the cluster that have the same VIP.
With that said, to allow VM guests to run NLB you need to set the VM property for “Enable spoofing of MACAddress”.
To enable spoofing of MAC Addresses open the Hyper-V management console. Make sure the VM is stoppedopen the properties of the VM. Select the Network Adaptor for the NLB VM and check the “Enable spoofing ofMAC Address” and click OK. Then start the VM.
[New Version] You can pass Microsoft 70-410 exam at the first time with Lead2pass 70-410 445q exam braindump, now you can also download free 70-410 test answers for VCE player and PDF files on the website.