2016 October Cisco Official New Released 400-101 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
We offers the most current and best training materials of the 400-101 certification Q&A , Practice Software, Study Packs, Preparation Labs and Audio Training you are looking for. Our online certification training offers you quick and cost-efficient way to train and become a certified professional in IT industry.
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-101.html
QUESTION 626
Which two statements about the default behavior of IS-IS are true? (Choose two.)
A. The default IS-IS router type is L1/L2.
B. The default IS-IS metric type is wide.
C. The default IS-IS interface circuit type is L1/L2.
D. By default, two IS-IS routers must use the same hello interval and hold timer in order to become neighbors.
Answer: AC
QUESTION 627
Which two statements about BPDU guard are true? (Choose two.)
A. The global configuration command spanning-tree portfast bpduguard default shuts down interfaces that are in the PortFast-operational state when a BPDU is received on that port.
B. The interface configuration command spanning-tree portfast bpduguard enable shuts down only interfaces with PortFast enabled when a BPDU is received.
C. BPDU guard can be used to prevent an access port from participating in the spanning tree in the service provider environment.
D. BPDU guard can be used to protect the root port.
E. BPDU guard can be used to prevent an invalid BPDU from propagating throughout the network.
Answer: AC
QUESTION 628
Which two 802.1D port states are expected in a stable Layer 2 network? (Choose two.)
A. forwarding
B. learning
C. listening
D. blocking
E. disabled
Answer: AD
QUESTION 629
Where must the spanning-tree timers be configured if they are not using the default timers?
A. They must be on the root bridge.
B. They must be on any non-root bridge.
C. Changing the default timers is not allowed.
D. Timers must be modified manually on each switch.
Answer: A
QUESTION 630
Which three fields are part of a TCN BPDU? (Choose three.)
A. protocol ID
B. version
C. type
D. max-age
E. flags
F. message age
Answer: ABC
QUESTION 631
With AutoInstall, which mechanism allows for automatic addressing of the serial interface using HDLC?
A. ARP
B. BOOTP
C. DHCP
D. SLARP
Answer: D
QUESTION 632
Which two protocols does the Management Plane Protection feature support? (Choose two.)
A. ARP
B. HTTPS
C. TFTP
D. OSPF
Answer: BC
QUESTION 633
Refer to the exhibit. Which configuration reduces CPU utilization on R2 while still advertising the connected routes of R2 to R1? 
A. Configure eigrp stub connected on R2.
B. Configure eigrp stub receive-only on R1.
C. Configure eigrp stub static on R2.
D. Configure eigrp stub summary on R1.
Answer: A
QUESTION 634
Which authentication types does OSPF support?
A. null and clear text
B. MD5 only
C. MD5 and clear text
D. null, clear text, and MD5
E. clear text only
Answer: D
QUESTION 635
Which ICMP message type is used to assist path MTU discovery?
A. destination unreachable
B. redirect message
C. source quench
D. time exceeded
Answer: A
QUESTION 636
A configuration includes the line ip route 10.0.0.0 255.0.0.0 172.16.10.10 permanent.
Which option is a benefit of configuring this static route as permanent?
A. It allows the route to be redistributed into the network even if the outgoing interface is down.
B. It allows the route to be saved in the running configuration of the device.
C. It places a hidden tag on the route that can be matched on other devices.
D. It allows the route to have a tracking status even if no tracking object is configured.
Answer: A
QUESTION 637
Refer to the exhibit. Which two statements about the R1 configuration are true? (Choose two.) 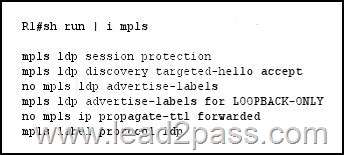
A. The IP TTL value is copied to the MPLS field during label imposition.
B. The structure of the MLPS network is hidden in a traceroute.
C. The LDP session interval and hold times are configured for directly connected neighbors.
D. R1 protects the session for 86400 seconds.
E. All locally assigned labels are discarded.
Answer: BD
QUESTION 638
Which two statements about IPsec VTI implementation are true? (Choose two.)
A. The IKE SA can be bound to the VTI and the crypto map.
B. The transform set can be configured only in tunnel mode.
C. SVTIs support only a single IPsec SA.
D. SVTIs support IPv4 packets that carry IPv6 packets.
Answer: BC
QUESTION 639
Which command sets the maximum segment size for a TCP packet initiated from a router?
A. ip mtu
B. ip tcp adjust-mss
C. ip tcp mss
D. ip tcp window-size
Answer: C
QUESTION 640
Which circumstance can cause TCP starvation and UDP dominance to occur?
A. Too few queues are available.
B. UDP is comprised of smaller packets than TCP.
C. Retransmitted TCP packets are on the network.
D. UDP and TCP data are assigned to the same service-provider class.
Answer: D
QUESTION 641
Refer to the exhibit. Which statement about the topology is true? 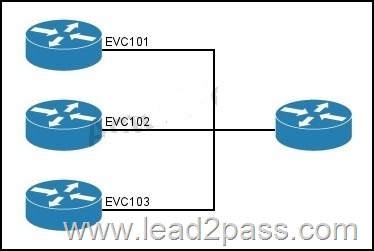
A. It provides a transparent LAN service.
B. It provides only point-to-multipoint connections between UNIs.
C. It uses port-based connections at the hub.
D. It provides point-to-point connections between UNIs.
Answer: D
QUESTION 642
Which two statements about reverse ARP are true? (Choose two.)
A. Its servers require static mappings.
B. It works with AutoInstall to configure new devices.
C. It provides IP addresses for subnet masks.
D. It provides IP addresses for default gateways.
E. It requires less maintenance than DHCP.
Answer: AB
QUESTION 643
Refer to the exhibit. This network is configured with PIM, and the RPF check has failed toward the multicast source. Which two configuration changes must you make to router R3 to enable the RPF check to pass? (Choose two.) 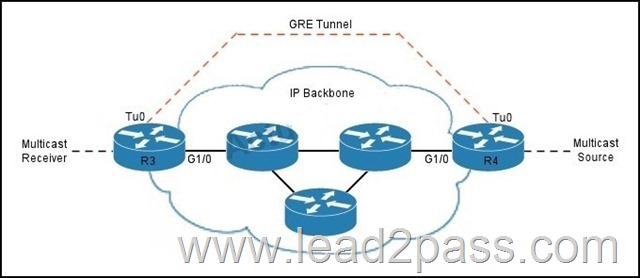
A. Configure a static multicast route to the multicast source through the tunnel interface.
B. Configure a static multicast route to the multicast source LAN through the tunnel interface.
C. Configure a static multicast route to the multicast source LAN through the Ethernet interface.
D. Remove the command ip prim bidir-enable from the R3 configuration.
Answer: AB
QUESTION 644
In which two situations is an EIGRP hello packet sent as unicast? (Choose two.)
A. during neighbor discovery
B. when link costs change
C. when the neighbor command is used
D. when an ACK is sent
Answer: CD
QUESTION 645
Which three options are results of the command no mpls ip propagate-ttl? (Choose three.)
A. It prevents the TTL from being copied from the IP header to the MPLS header.
B. It prevents the MPLS hops from being visible to a CE router when you perform a traceroute.
C. A fixed TTL value of 255 is used for the first label of the IP packet.
D. It prevents the TTL from being copied from the MPLS header back into the IP header.
E. MPLS hops remain visible on a CE router when you perform a traceroute.
F. A fixed TTL value of 1 is used for the first label of the IP packet.
Answer: ABC
QUESTION 646
Which statement about how a CE router is used in an MPLS VPN is true?
A. It is located on the customer premises, where it peers and exchanges routes with the provider edge router.
B. It is located on the provider premises, where it peers and exchanges routes with the customer edge router.
C. It is located on the customer premises, but it is fully controlled by the provider, which provides a full routing table to the customer.
D. It is located on the provider premises, and it routes only MPLS label traffic.
Answer: A
QUESTION 647
Which three options are three benefits of an MPLS VPN? (Choose three.)
A. It allows IP address space overlap by maintaining customer routes in a private routing table.
B. It offers additional security by preventing intrusions directly into the customer routing table.
C. It offers a transparent virtual network in which all customer sites appear on one LAN.
D. It offers additional security by allowing only dynamic routing protocols between CE and PE routers.
E. It allows IP address space overlap by maintaining customer routes in the global routing table with unique BGP communities.
F. Providers can send only a default route for Internet access into the customer VPN.
Answer: ABC
QUESTION 648
Into which two pieces of information does the LISP protocol split the device identity? (Choose two.)
A. Routing Locator
B. Endpoint Identifier
C. Resource Location
D. Enterprise Identifier
E. LISP ID
F. Device ID
Answer: AB
QUESTION 649
Which two protocols are used to establish IPv6 connectivity over an MPLS network? (Choose two.)
A. 6PE
B. 6VPE
C. RSVP
D. ISATAP
E. LDP
F. IPv6IP
Answer: AB
QUESTION 650
Which three types of traffic are protected when you implement IPsec within an IPv6-in-IPv4 tunnel? (Choose three.)
A. IPv6 link-local traffic
B. IPv6 multicast traffic
C. IPv6 unicast traffic
D. IPv4 tunnel control traffic
E. IPv4 broadcast traffic
F. IPv6 broadcast traffic
Answer: ABC
The strength of our 400-101 dumps is the constant update that we perform to keep abreast with the market trends and changes. Our 400-101 exam question is not only the best option for certification but also enhances your skill to an advance level.
400-101 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU2RjeUlHTTZXb1U
2016 Cisco 400-101 exam dumps (All 1219 Q&As) from Lead2pass:
http://www.lead2pass.com/400-101.html [100% Exam Pass Guaranteed]