Lead2pass 70-698 Dumps PDF Free Download:
https://www.lead2pass.com/70-698.html
QUESTION 21
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
You have a computer named Computer1 that runs Windows 10.
File History is turned on.
The user of Computer1 reports that previous versions of D:\Folder\File1 doc are unavailable from the Previous Versions tab.
You need to ensure that the previous versions of the file are created
Solution: Add D:\Folder\to the Documents library.
Does this meet the goal?
A. Yes
B. No
Answer: A
Explanation:
https://support.microsoft.com/en-us/help/17128/windows-8-file-history
QUESTION 22
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
A user named User1 is a member of the local Administrators group on Computer1 and Computer2. User1 fails to access the Event Viewer logs on Computer 2 from Computer 1.
User1 can connect to Computed remotely by using Computer Management.
You need to ensure that User1 can use Event Viewer on Computer1 to remotely view the Event Viewer logs on Computer 2.
Solution: You run Enable-PSRemoting on Computer 1.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
http://www.howtogeek.com/117192/how-to-run-powershell-commands-on-remote-computers/
QUESTION 23
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
A user named User1 is a member of the local Administrators group on Computer1 and Computer2. User1 fails to access the Event Viewer logs on Computer 2 from Computer 1.
User1 can connect to Computed remotely by using Computer Management.
You need to ensure that User1 can use Event Viewer on Computer1 to remotely view the Event Viewer logs on Computer 2.
Solution: You run winrm quick config on Computer2.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
https://msdn.microsoft.com/en-us/library/aa384372(v=vs.85).aspx
QUESTION 24
Note: This question is part of a series of questions that use the same scenario.
For your convenience, the scenario is repeated in each question.
Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario
Your network contains a single Active Directory domain named adatum.com.
The network contains five servers configured as shown in the following table.
All of the servers run Windows Server 2012 R2.
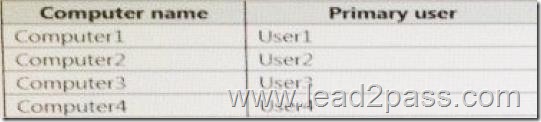
Test_Server has a shared folder named ShareA. Only local users have permissions to ShareA. The network contains a mainframe computer that is administered by using the Telnet protocol. The domain contains four client computers configured as shown in the following table.
All of the client computers run the 64-bit version of Windows.
User3 frequently accesses ShareA.
Remote Desktop is enabled on Computer4.
Your company identifies the following requirements:
– Ensure that you can test unsigned device drivers on Computer1
– Enable Credential Guard on Computer2.
– Run commands and cmdlets remotely on computer2.
– Configure User Account control (UAC) on Computer3 to prompt administrators for credentials when elevated privileges are required.
– Ensure that User1 can view and interact with a desktop session of User3.
– Ensure that User2 can use Telnet to manage the mainframe.
– Ensure that User4 can use Remote Desktop to access Computer4 remotely.
End of repeated scenario.
You need to configure Computer3 to meet the UAC requirement. What should you use?
A. User Account Control Settings
B. Credential Manager
C. Security Options in the Computer Configuration of the Local Computer Policy.
D. Security Settings in the User Computer of the Local Computer Policy.
Answer: C
Explanation:
http://www.ghacks.net/2013/06/20/how-to-configure-windows-uac-prompt-behavior-for-admins-and-users/
QUESTION 25
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario
Your network contains a single Active Directory domain named adatum.com.
The network contains five servers configured as shown in the following table.
All of the servers run Windows Server 2012 R2.
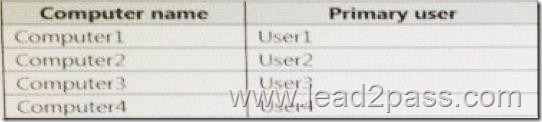
Test_Server has a shared folder named ShareA. Only local users have permissions to ShareA. The network contains a mainframe computer that is administered by using the Telnet protocol. The domain contains four client computers configured as shown in the following table.
All of the client computers run the 64-bit version of Windows.
User3 frequently accesses ShareA.
Remote Desktop is enabled on Computer4.
Your company identifies the following requirements:
– Ensure that you can test unsigned device drivers on Computer1
– Enable Credential Guard on Computer2.
– Run commands and cmdlets remotely on computer2.
– Configure User Account control (UAC) on Computer3 to prompt administrators for credentials when elevated privileges are required.
– Ensure that User1 can view and interact with a desktop session of User3.
– Ensure that User2 can use Telnet to manage the mainframe.
– Ensure that User4 can use Remote Desktop to access Computer4 remotely.
End of repeated scenario.
On Test_Server, you reset the password for User3.
You need to ensure that User3 can access ShareA.
Which tool should you instruct User3 to use on Computer3?
A. the Get-Credential cmdlet
B. Credential Manager
C. Authorization Manager
D. Active Directory Users and Computers
Answer: B
Explanation:
http://www.digitalcitizen.life/credential-manager-where-windows-stores-passwords-other-login-details
QUESTION 26
Note: This question is part of a series of questions that use the same scenario. For your convenience, the scenario is repeated in each question. Each question presents a different goal and answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario
Your network contains a single Active Directory domain named adatum.com.
The network contains five servers configured as shown in the following table.
All of the servers run Windows Server 2012 R2.
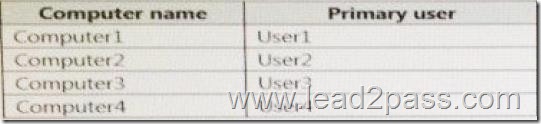
Test_Server has a shared folder named ShareA. Only local users have permissions to ShareA. The network contains a mainframe computer that is administered by using the Telnet protocol. The domain contains four client computers configured as shown in the following table.
All of the client computers run the 64-bit version of Windows.
User3 frequently accesses ShareA.
Remote Desktop is enabled on Computer4.
Your company identifies the following requirements:
– Ensure that you can test unsigned device drivers on Computer1
– Enable Credential Guard on Computer2.
– Run commands and cmdlets remotely on computer2.
– Configure User Account control (UAC) on Computer3 to prompt administrators for credentials when elevated privileges are required.
– Ensure that User1 can view and interact with a desktop session of User3.
– Ensure that User2 can use Telnet to manage the mainframe.
– Ensure that User4 can use Remote Desktop to access Computer4 remotely.
End of repeated scenario.
You need to meet the Credential Guard requirement of Computer2. Which two Windows features should you install? Each correct answer presents part of the solution.
A. Windows Process Activation Service (WAS)
B. Embedded Boot Experience
C. Isolated User Mode
D. Windows Identity Foundation 3.5
E. Hyper-V Hypervisor
Answer: CE
Explanation:
https://technet.microsoft.com/en-us/itpro/windows/keep-secure/credential-guard
70-698 dumps full version (PDF&VCE): https://www.lead2pass.com/70-698.html
Large amount of free 70-698 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDa2cwaDdKY1dLdHM
You may also need:
70-697 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDX3RYMG04cEg5aEE