Hi this is Myles Joseph from Austrail and I would like to tell you that I passed my SY0-501 exam with the use of Lead2pass SY0-501 Exam Questions. I got same questions in my exam that I prepared from your test engine software. I will recommend your site to all my friends for sure.
Following questions and answers are all new published by CompTIA Official Exam Center: https://www.lead2pass.com/sy0-501.html
QUESTION 131
An attacker compromises a public CA and issues unauthorized X.509 certificates for Company.com. In the future, impact of similar incidents. Which of the following would assist Company.com with its goal?
A. Certificate pinning
B. Certificate stapling
C. Certificate chaining
D. Certificate with extended validation
Answer: D
QUESTION 132
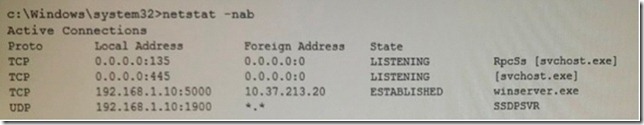
After a user reports stow computer performance, a systems administrator detects a suspicious file, which was installed as part of a freeware software package.
The systems administrator reviews the output below:
Based on the above information, which of the following types of malware was installed on the user’s computer?
A. Keylogger
B. Spyware
C. Worm
D. Bot
Answer: B
QUESTION 133
Drag and Drop Questions
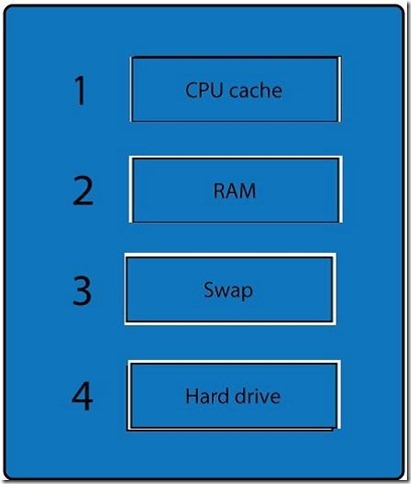
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.
Answer:
Explanation:
When dealing with multiple issues, address them in order of volatility (OOV); always deal with the most volatile first. Volatility can be thought of as the amount of time that you have to collect certain data before a window of opportunity is gone. Naturally, in an investigation you want to collect everything, but some data will exist longer than others, and you cannot possibly collect all of it once. As an example, the OOV in an investigation may be RAM, hard drive data, CDs/DVDs, and printouts.
Order of volatility: Capture system images as a snapshot of what exists, look at network traffic and logs, capture any relevant video/screenshots/hashes, record time offset on the systems, talk to witnesses, and track total man-hours and expenses associated with the investigation.
QUESTION 134
Malicious traffic from an internal network has been detected on an unauthorized port on an application server. Which of the following network-based security controls should the engineer consider implementing?
A. ACLs
B. HIPS
C. NAT
D. MAC filtering
Answer: D
QUESTION 135
A company wants to host a publicly available server that performs the following functions:
Evaluates MX record lookup
Can perform authenticated requests for A and AAA records
Uses RRSIG
Which of the following should the company use to fulfill the above requirements?
A. DNSSEC
B. SFTP
C. nslookup
D. dig
Answer: C
QUESTION 136
Which of the following attack types BEST describes a client-side attack that is used to mandate an HTML iframe with JavaScript code via web browser?
A. MITM
B. xss
C. SQLi
Answer: B
QUESTION 137
A company has a data classification system with definitions for “Private” and public.” The company’s security policy outlines how data should be protected based on type. The company recently added the data type “Proprietary” Which of the following is the MOST likely reason the company added this data type?
A. Reduced cost
B. More searchable data
C. Better data classification
D. Expanded authority of the privacy officer
Answer: B
QUESTION 138
A security administrator is developing training for corporate users on basic security principles for personal email accounts.
Which of the following should be mentioned as the MOST secure way for password recovery?
A. Utilizing a single Qfor password recovery
B. Sending a PIN to a smartphone through text message
C. Utilizing CAPTCHA to avoid brute force attacks
D. Use a different e-mail address to recover password
Answer: B
QUESTION 139
A company researched the root cause of a recent vulnerability in its software. It was determined that the vulnerability was the result of two updates made in the last release. Each update alone would not have resulted in the vulnerability.
In order to prevent similar situations in the future, the company should improve which of the following?
A. Change management procedures
B. Job rotation policies
C. Incident response management
D. Least privilege access controls
Answer: A
QUESTION 140
A computer on a company network was infected with a zero-day exploit after an employee accidently opened an email that contained malicious content. The employee recognized the email as malicious and was attempting to delete it, but accidently opened it.
Which of the following should be done to prevent this scenario from occurring again in the future?
A. Install host-based firewalls on all computers that have an email client installed
B. Set the email program default to open messages in plain text
C. Install end-point protection on all computers that access web email
D. Create new email spam filters to delete all messages from that sender
Answer: C
More free Lead2pass SY0-501 exam new questions on Google Drive: https://drive.google.com/open?id=1Hm6GQHDVOsEnyhNf3EHqIGEtor5IUsfu
Lead2pass offers free demo for SY0-501 exam. You can also check demo of SY0-501 practice exams before you decide to buy it.
2017 CompTIA SY0-501 (All 166 Q&As) exam dumps (PDF&VCE) from Lead2pass:
https://www.lead2pass.com/sy0-501.html [100% Exam Pass Guaranteed]