Lead2pass Dumps For Exam 400-251 With New Updated Exam Questions:
https://www.lead2pass.com/400-251.html
QUESTION 31
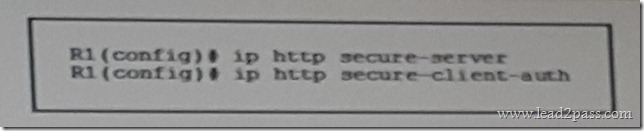
Refer to the exhibit. What is the effect of the given command sequence?
A. The HTTP server and client will negotiate the cipher suite encryption parameters.
B. The server will accept secure HTTP connections from clients with signed security certificates.
C. The client profile will match the authorization profile defined in the AAA server.
D. The clients are added to the cipher suite’s profile.
E. The server will accept secure HTTP connections form clients defined in the AAA server.
Answer: B
QUESTION 32
In ISO 27002, access control code of practice for information Security Management servers which of the following objective?
A. Implement protocol control of user, network and application access
B. Optimize the audit process
C. Prevent the physical damage of the resources
D. Educating employees on security requirements and issues
Answer: A
QUESTION 33
Which two options are differences between a automation and orchestration? (Choose two)
A. Automation is an IT workflow composed of tasks, and orchestration is a technical task.
B. Orchestration is focused on multiple technologies to be integrated together.
C. Orchestration is focused on an end-to-end process or workflow
D. Automation is to be used to replace human intervention.
E. Automation is focused on automating a single or multiple tasks.
Answer: CE
QUESTION 34
What is the first step in performing a risk assessment?
A. Identifying critical services and network vulnerabilities and determining the potential impact of their compromise or failure.
B. Investigating reports of data theft or security breaches and assigning responsibility.
C. Terminating any employee believed to be responsible for compromising security.
D. Evaluating the effectiveness and appropriateness of the organization’s current risk-management activities.
E. Establishing a security team to perform forensic examinations of previous known attacks.
Answer: A
QUESTION 35
Which description of a virtual private cloud is true?
A. An on-demand configurable pool of shared software applications allocated within a public cloud environment, which provides tenant isolation
B. An on-demand configurable pool of shared data resources allocated within a private cloud environment, which provides assigned DMZ zones
C. An on-demand configurable pool of shared networking resources allocated within a private cloud environment, which provides tenant isolation
D. An on-demand configurable pool of shared computing resources allocated within a public cloud environment, which provides tenant isolation
Answer: D
QUESTION 36
On which two protocols is VNC based? (Choose two)
A. Rdesktop
B. UDP
C. RFB
D. Terminal Services Client
E. CoRD
F. TCP
Answer: CF
QUESTION 37
How can the tail drop algorithem support traffic when the queue is filled?
A. It drop older packet with a size of 64 byts or more until queue has more traffic
B. It drop older packet with a size of less than 64 byts until queue has more traffic
C. It drops all new packets until the queue has room for more traffic
D. It drops older TCP packets that are set to be redelivered due to error on the link until the queue has room for more traffic.
Answer: C
QUESTION 38
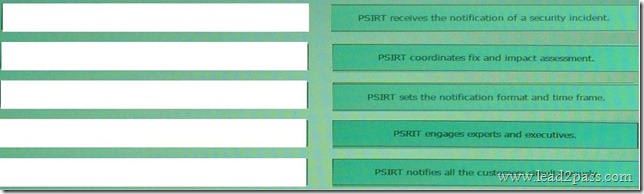
Drag and Drop Question
Drag each step in the cisco PRIST response to incidents and vulnerability involving cisco product on the left into the correct order on the right.
Answer:
QUESTION 39
Which two statements about the 3DES encryption protocol are true? (Choose two)
A. It can operate in the Electronic Code Book and Asymmetric Block Chaining modes.
B. Its effective key length is 168 bits.
C. It encrypts and decrypts data in three 64-bit blocks with an overall key length of 192 bits.
D. The algorithm is most efficient when it is implemented in software instead of hardware.
E. It encrypts and decrypts data in three 56-bit blocks with an overall key length of 168 bits.
F. Its effective key length is 112 bits.
Answer: BC
QUESTION 40
You want to enable users in your company’s branch offices to deploy their own access points using WAN link from the central office, but you are unable to a deploy a controller in the branch offices. What lightweight access point wireless mode should you choose?
A. TLS mode
B. H-REAP mode
C. Monitor mode
D. REAP mode
E. Local mode
Answer: B
400-251 dumps full version (PDF&VCE): https://www.lead2pass.com/400-251.html
Large amount of free 400-251 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU1JrNmttR1dfUm8