2016 September Cisco Official New Released 210-260 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
2016 get prepared with fully updated Cisco 210-260 real exam questions and accurate answers for 210-260 exam. Lead2pass IT experts review the 210-260 newly added questions and offer correct Cisco 210-260 exam questions answers. 100% pass easily!
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/210-260.html
QUESTION 21
Which command is needed to enable SSH support on a Cisco Router?
A. crypto key lock rsa
B. crypto key generate rsa
C. crypto key zeroize rsa
D. crypto key unlock rsa
Answer: B
QUESTION 22
In which three ways does the TACACS protocol differ from RADIUS? (Choose three)
A. TACACS uses TCP to communicate with the NAS
B. TACACS can encrypt the entire packet that is sent to the NAS
C. TACACS authenticates and authorizes simultaneously, causing fewer packets to be transmitted
D. TACACS uses UDP to communicate with the NAS
E. TACACS encrypts only the password field in an authentication packet
F. TACACS support per-command authorization
Answer: ABF
QUESTION 23
Scenario
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first. 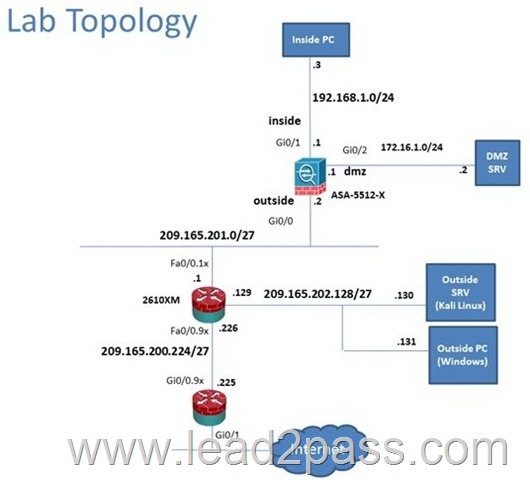
Which user authentication method is used when users login to the Clientless SSL VPN portal using https://209165.201.2/test?
A. Both Certificate and AAA with LOCAL database
B. AAA with RADIUS server
C. Both Certificate and AAA with RADIUS server
D. AAA with LOCAL database
E. Certificate
Answer: D
Explanation:
This can be seen from the Connection Profiles Tab of the Remote Access VPN configuration,
where the alias of test is being used.
QUESTION 24
Scenario
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first. 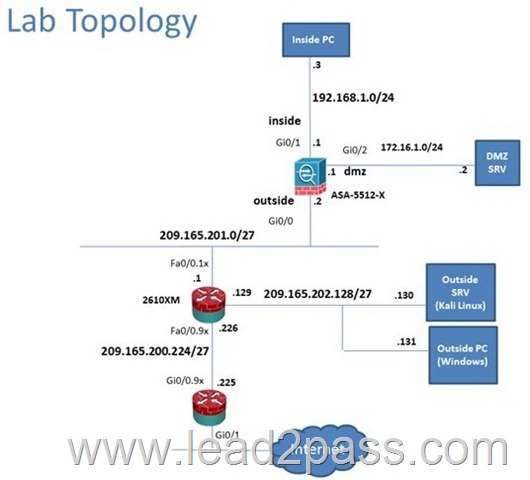
When users login to the Clientless SSL VPN using https://209.165.201.2/test, which group policy will be applied?
A. test
B. Sales
C. DefaultRAGroup
D. DefaultWEBVPNGroup
E. clientless
F. DFTGrpPolicy
Answer: B
Explanation:
First navigate to the Connection Profiles tab as shown below, highlight the one with the test alias:
Then hit the “edit” button and you can clearly see the Sales Group Policy being applied.
QUESTION 25
Scenario
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first. 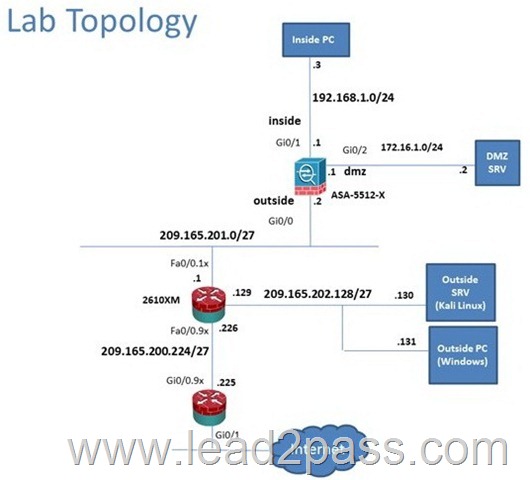
Which two statements regarding the ASA VPN configurations are correct? (Choose two)
A. The Inside-SRV bookmark has not been applied to the Sales group policy
B. The ASA has a certificate issued by an external Certificate Authority associated to the ASDM_Trustpoint1
C. The Inside-SRV bookmark references the https://10.x.x.x URL
D. Any Connect, IPSec IKEv1 and IPSec IKEv2 VPN access is enabled on the outside interface
E. Only Clientless SSL VPN VPN access is allowed with the Sales group Policy
F. The DefaultWEBVPNGroup Connection Profile is using the AAA with Radius server method
Answer: EF
Explanation:
In the real If appear in the option answers an ip like https://10... URL and not https://192.168.1.2 URL then the answers will be EF.
QUESTION 26
Scenario
In this simulation, you have access to ASDM only. Review the various ASA configurations using ASDM then answer the five multiple choice questions about the ASA SSLVPN configurations.
To access ASDM, click the ASA icon in the topology diagram.
Note: Not all ASDM functionalities are enabled in this simulation.
To see all the menu options available on the left navigation pane, you may also need to un-expand the expanded menu first. 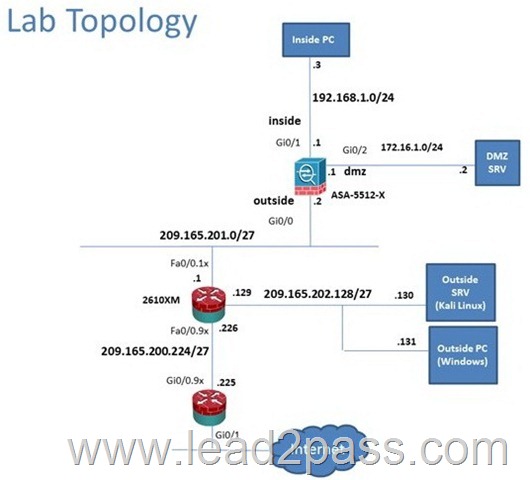
Which four tunneling protocols are enabled in the DfltGrpPolicy group policy? (choose four)
A. IPsec IKEv1
B. IPsec IKEv2
C. L2TP/IPsec
D. Clientless SSL VPN
E. SSL VPN Client
F. PPTP
Answer: ABCD
Explanation:
By clicking one the Configuration-> Remote Access -> Clientless CCL VPN Access-> Group Policies tab you can view the DfltGrpPolicy protocols as shown below:
QUESTION 27
Scenario
Given the new additional connectivity requirements and the topology diagram, use ASDM to accomplish the required ASA configurations to meet the requirements.
New additional connectivity requirements:
– Currently, the ASA configurations only allow on the Inside and DMZ networks to access any hosts on the Outside. Your task is to use ASDM to configure the ASA to also allow any host only on the Outside to HTTP to the DMZ server. The hosts on the Outside will need to use the 209.165.201.30 public IP address when HTTPing to the DMZ server.
– Currently, hosts on the ASA higher security level interfaces are not able to ping any hosts on the lower security level interfaces. Your task in this simulation is to use ASDM to enable the ASA to dynamically allow the echo-reply responses back through the ASA.
Once the correct ASA configurations have been configured:
– You can test the connectivity tohttp://209.165.201,30from the Outside PC browser.
– You can test the pings to the Outside (www.cisco.com) by opening the inside PC command prompt window. In this simulation, only testing pings to www.cisco.com will work.
To access ASDM, click the ASA icon in the topology diagram.
To access the Firefox Browser on the Outside PC, click the Outside PC icon in the topology diagram.
To access the Command prompt on the Inside PC, click the Inside PC icon in the topology diagram.
Note:
After you make the configuration changes in ASDM, remember to click Apply to apply the configuration changes.
Not all ASDM screens are enabled in this simulation, if some screen is not enabled, try to use different methods to configure the ASA to meet the requirements.
In this simulation, some of the ASDM screens may not look and function exactly like the real ASDM. 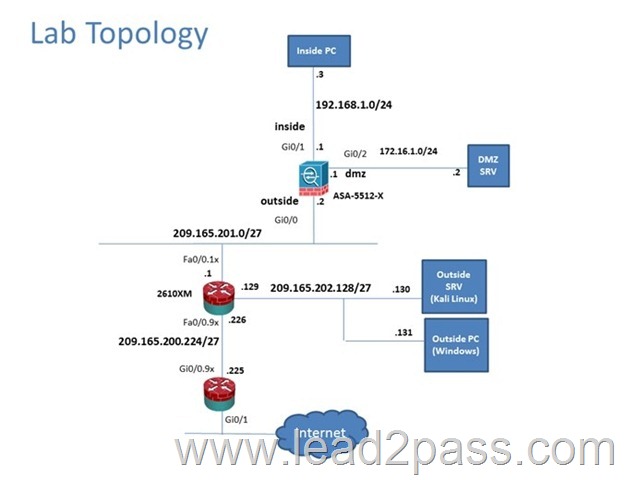
Answer:
Step 1: Firewall, Configuration, NAT Rules, Name=WebSvr, IP version IPv4, IP address=172.16.1.2 Static NAT=209.165.201.30
Step 2: Firewall, Config, Access Rules, Interface=Outside, Action=Permit, Source=any, Destination=209.165.201.30, Service=tcp/http
Step 3: Firewall, Config, Service policy Rules, Click Global Policy and edit, Rule Action tab, Click ICMP and apply
Step 4: Ping www.cisco.com from Inside PC
Step 5: Type http://209.165.201.30 in web browser in the Outside PC
Explanation:
First, for the HTTP access we need to creat a NAT object. Here I called it HTTP but it can be given any name.
Then, create the firewall rules to allow the HTTP access:
You can verify using the outside PC to HTTP into 209.165.201.30.
For step two, to be able to ping hosts on the outside, we edit the last service policy shown below:
And then check the ICMP box only as shown below, then hit Apply.
After that is done, we can ping www.cisco.com again to verify:
QUESTION 28
What is the purpose of the Integrity component of the CIA triad?
A. to ensure that only authorized parties can modify data
B. to determine whether data is relevant
C. to create a process for accessing data
D. to ensure that only authorized parties can view data
Answer: A
QUESTION 29
Which two statements about Telnet access to the ASA are true? (Choose two).
A. You may VPN to the lowest security interface to telnet to an inside interface.
B. You must configure an AAA server to enable Telnet.
C. You can access all interfaces on an ASA using Telnet.
D. You must use the command virtual telnet to enable Telnet.
E. Best practice is to disable Telnet and use SSH.
Answer: AE
QUESTION 30
Which protocol provides security to Secure Copy?
A. IPsec
B. SSH
C. HTTPS
D. ESP
Answer: B
Latest 210-260 questions and answers from Cisco Exam Center offered by Lead2pass for free share now! Read and remember all real questions answers, Guarantee pass 210-260 real test 100% or full money back!
210-260 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDLWhBVC0zekJKUUU
2016 Cisco 210-260 exam dumps (All 193 Q&As) from Lead2pass:
http://www.lead2pass.com/210-260.html [100% Exam Pass Guaranteed]