2016 September Cisco Official New Released 100-105 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
2016 get prepared with fully updated Cisco 100-105 real exam questions and accurate answers for 100-105 exam. Lead2pass IT experts review the 100-105 newly added questions and offer correct Cisco 100-105 exam questions answers. 100% pass easily!
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/100-105.html
QUESTION 171
Which of the following are types of flow control? (Choose three.)
A. buffering
B. cut-through
C. windowing
D. congestion avoidance
E. load balancing
Answer: ACD
Explanation:
http://www.info-it.net/cisco/ccna/exam-tips/flow-control.php
During Transfer of data, a high speed computer is generating data traffic a lot faster than the network device can handle in transferring to destination, so single gateway or destination device cannot handle much amount of traffic that is called “Congestion”.
Buffering
The Technie is used to control the data transfer when we have congestion, when a network device receive a data it stores in memory section and then transfer to next destination this process called “Buffering”.
Windowing Whereas Windowing is used for flow control by the Transport layer. Say the sender device is sending segments and the receiver device can accommodate only a fixed number of segments before it can accept more, the two devices negotiate the window size during the connection setup.
This is done so that the sending device doesn’t overflow the receiving device’s buffer. Also the receiving device can send a single acknowledgement for the segments it has received instead of sending an acknowledgement after every segment received. Also, this window size is dynamic meaning, the devices can negotiate and change the window size in the middle of a session. So if initially the window size is three and the receiving device thinks that it can accept more number of segments in its buffer it can negotiate with the sending device and it increase it to say 5 for example. Windowing is used only by TCP since UDP doesn’t use or allow flow control.
QUESTION 172
How many simultaneous Telnet sessions does a Cisco router support by default?
A. 1
B. 2
C. 3
D. 4
E. 5
F. 6
Answer: E
QUESTION 173
What is the purpose of flow control?
A. To ensure data is retransmitted if an acknowledgement is not received.
B. To reassemble segments in the correct order at the destination device.
C. To provide a means for the receiver to govern the amount of data sent by the sender.
D. To regulate the size of each segment.
Answer: C
Explanation:
http://whatis.techtarget.com/definition/flow-control Flow control is the management of data flow between computers or devices or between nodes in a network so that the data can be handled at an efficient pace. Too much data arriving before a device can handle it causes data overflow, meaning the data is either lost or must be retransmitted. For serial data transmission locally or in a network, the Xon/Xoff protocol can be used. For modem connections, either Xon/Xoff or CTS/RTS (Clear to Send/Ready to Send) commands can be used to control data flow. In a network, flow control can also be applied by refusing additional device connections until the flow of traffic has subsided.
QUESTION 174
Refer to the exhibit. How many collision domains are shown? 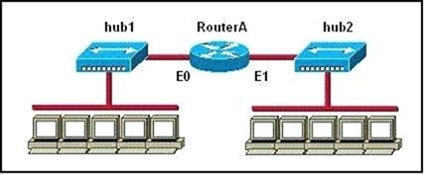
A. one
B. two
C. three
D. four
E. six
F. twelve
Answer: B
Explanation:
Hubs create single collision and broadcast domains.
QUESTION 175
Which IP address is a private address?
A. 12.0.0.1
B. 168.172.19.39
C. 172.20.14.36
D. 172.33.194.30
E. 192.169.42.34
Answer: C
QUESTION 176
Which statement is true?
A. An IPv6 address is 64 bits long and is represented as hexadecimal characters.
B. An IPv6 address is 32 bits long and is represented as decimal digits.
C. An IPv6 address is 128 bits long and is represented as decimal digits.
D. An IPv6 address is 128 bits long and is represented as hexadecimal characters.
Answer: D
Explanation:
http://www.cisco.com/en/US/technologies/tk648/tk872/technologies_white_paper0900aecd 8026003d.pdf
One of the key advantages IPv6 brings is the exponentially larger address space. The following will outline the basic address architecture of IPv6.
128-bit-long addresses
Represented in hexadecimal format:
Uses CIDR principles: prefix/prefix length
x:x:x:x:x:x:x:x, where x is a 16-bit hex field
The last 64 bits are used for the interface ID
QUESTION 177
If an Ethernet port on a router was assigned an IP address of 172.16.112.1/20, what is the maximum number of hosts allowed on this subnet?
A. 1024
B. 2046
C. 4094
D. 4096
E. 8190
Answer: C
Explanation:
Each octet represents eight bits. The bits, in turn, represent (from left to right): 128, 64, 32 , 16 , 8, 4, 2, 1
Add them up and you get 255. Add one for the all zeros option, and the total is 256. Now take away one of these for the network address (all zeros) and another for the broadcast address (all ones). Each octet represents 254 possible hosts. Or 254 possible networks. Unless you have subnet zero set on your network gear, in which case you could conceivably have 255.
The CIDR addressing format (/20) tells us that 20 bits are used for the network portion, so the maximum number of networks are 2^20 minus one if you have subnet zero enabled, or minus 2 if not.
You asked about the number of hosts. That will be 32 minus the number of network bits, minus two. So calculate it as (2^(32-20))-2, or (2^12)-2 = 4094
QUESTION 178
Which statements are TRUE regarding Internet Protocol version 6 (IPv6) addresses? (Choose three.)
A. An IPv6 address is divided into eight 16-bit groups.
B. A double colon (::) can only be used once in a single IPv6 address.
C. IPv6 addresses are 196 bits in length.
D. Leading zeros cannot be omitted in an IPv6 address.
E. Groups with a value of 0 can be represented with a single 0 in IPv6 address.
Answer: ABE
Explanation:
IPv6 addresses are divided into eight 16-bit groups, a double colon (::) can only be used once in an IPv6 address, and groups with a value of 0 can be represented with a single 0 in an IPv6 address.
The following statements are also true regarding IPv6 address:
IPv6 addresses are 128 bits in length.
Eight 16-bit groups are divided by a colon (:).
Multiple groups of 16-bit 0s can be represented with double colon (::).
Double colons (::) represent only 0s.
Leading zeros can be omitted in an IPv6 address.
The option stating that IPv6 addresses are 196 bits in length is incorrect. IPv6 addresses are 128 bits in length.
The option stating that leading zeros cannot be omitted in an IPv6 address is incorrect.
Leading zeros can be omitted in an IPv6 address.
QUESTION 179
Which of the following IP addresses are valid Class B host addresses if a default Class B mask is in use? (Choose two.)
A. 10.6.8.35
B. 133.6.5.4
C. 192.168.5.9
D. 127.0.0.1
E. 190.6.5.4
Answer: BE
Explanation:
The IP addresses 133.6.5.4 and 190.6.5.4 are both valid Class B addresses when a default mask is in use.
The Class B default mask is 255.255.0.0 and the range of valid addresses is 128.0.0.0- 191.255.255.255.
The IP address 10.6.8.35 is a Class A address. The Class A default mask is 255.0.0.0 and the range of valid addresses is 1.0.0.0 – 127.255.255.255, with the exception of the range 127.0.0.1 – 127.255.255.255, which is reserved and cannot be assigned. The IP address 192.168.5.9 is a Class C address. The Class C default mask is 255.255.255.0 and the range of valid addresses is 192.0.0.0 – 223.255.255.255. The IP address 127.0.0.1 is a Class A address, but it comes from a reserved portion that cannot be assigned.
The range 127.0.0.1 – 127.255.255.255 is used for diagnostics, and although any address in the range will work as a diagnostic address, 127.0.0.1 is known as the loopback address. If you can ping this address, or any address in the 127.0.0.1 – 127.255.255.255 range, then the NIC is working and TCP/IP is installed. The Class A default mask is 255.0.0.0 and the range of valid addresses is 1.0.0.0 – 127.255.255.255, with the exception of the range 127.0.0.1 – 127.255.255.255, which is reserved and cannot be assigned.
QUESTION 180
How many addresses will be available for dynamic NAT translation when a router is configured with the following commands?
Router(config)#ip nat pool TAME 209.165.201.23 209.165.201.30 netmask 255.255.255.224
Router(config)#ip nat inside source list 9 pool TAME
A. 7
B. 8
C. 9
D. 10
E. 24
F. 32
Answer: B
Explanation:
209.165.201.23 to 209.165.201.30 provides for 8 addresses.
QUESTION 181
Some routers have been configured with default routes.
What are some of the advantages of using default routes? (Choose two)
A. They establish routes that will never go down.
B. They keep routing tables small.
C. They require a great deal of CPU power.
D. They allow connectivity to remote networks that are not in the routing table
E. They direct traffic from the internet into corporate networks.
Answer: BD
Explanation:
Cisco administration 101: What you need to know about default routes
http://www.techrepublic.com/article/cisco-administration-101-what-you-need-to-know-about-default-routes/
QUESTION 182
Refer to the exhibit. PC1 pings PC2. What three things will CORE router do with the data that is received from PC1? (Choose three.) 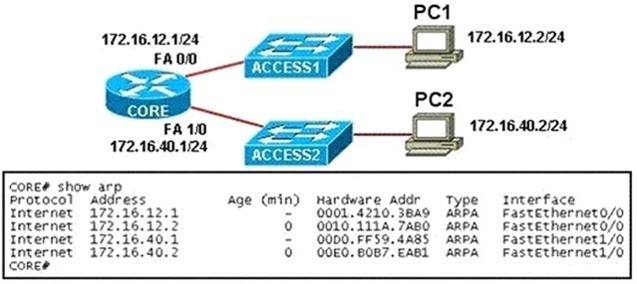
A. The data frames will be forwarded out interface FastEthernet0/1 of CORE router.
B. The data frames will be forwarded out interface FastEthernet1/0 of CORE router.
C. CORE router will replace the destination IP address of the packets with the IP address of PC2.
D. CORE router will replace the MAC address of PC2 in the destination MAC address of the frames.
E. CORE router will put the IP address of the forwarding FastEthernet interface in the place of the
source IP address in the packets.
F. CORE router will put the MAC address of the forwarding FastEthernet interface in the place of the
source MAC address.
Answer: BDF
QUESTION 183
Which three statements are correct about RIP version 2? (Choose three)
A. It uses broadcast for its routing updates.
B. It supports authentication.
C. It is a classless routing protocol.
D. It has a lower default administrative distance then RIP version 1.
E. It has the same maximum hop count as RIP version 1.
F. It does not send the subnet mask any updates.
Answer: BCE
QUESTION 184
Refer to the exhibit. Why are two OSPF designated routers identified on Core-Router? 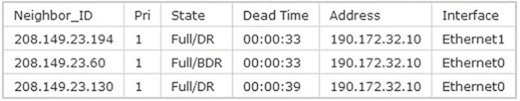
A. Core-Router is connected to more than one multi-access network.
B. The router at 208.149.23.130 is a secondary DR in case the primary fails.
C. Two router IDs have the same OSPF priority and are therefore tied for DR election
D. The DR election is still underway and there are two contenders for the role.
Answer: A
Explanation:
OSPF elects one DR per multi-access network. In the exhibit there are two DR so there must have more than one multi-access network.
QUESTION 185
What is the OSPF default frequency, in seconds, at which a Cisco router sends hello packets on a multi-access network?
A. 10
B. 40
C. 30
D. 20
Answer: A
Explanation:
On broadcast multiacess and point-to-point links, the default is 10 seconds. On NBMA, the default is 30 seconds.
QUESTION 186
What does the “Inside Global” address represent in the configuration of NAT?
A. the summarized address for all of the internal subnetted addresses
B. the MAC address of the router used by inside hosts to connect to the Internet
C. a globally unique, private IP address assigned to a host on the inside network
D. a registered address that represents an inside host to an outside network
Answer: D
Explanation:
NAT: Local and Global Definitions
http://www.cisco.com/en/US/tech/tk648/tk361/technologies_tech_note09186a0080094837.
shtml
Cisco defines these terms as:
Inside local address–The IP address assigned to a host on the inside network. This is the address configured as a parameter of the computer OS or received via dynamic address allocation protocols such as DHCP. The address is likely not a legitimate IP address assigned by the Network Information Center (NIC) or service provider. Inside global address–A legitimate IP address assigned by the NIC or service provider that represents one or more inside local IP addresses to the outside world. Outside local address–The IP address of an outside host as it appears to the inside network. Not necessarily a legitimate address, it is allocated from an address space routable on the inside.
Outside global address–The IP address assigned to a host on the outside network by the host owner.
The address is allocated from a globally routable address or network space. These definitions still leave a lot to be interpreted. For this example, this document redefines these terms by first defining local address and global address. Keep in mind that the terms inside and outside are NAT definitions. Interfaces on a NAT router are defined as inside or outside with the NAT configuration commands, ip nat inside destination and ip nat outside source . Networks to which these interfaces connect can then be thought of as inside networks or outside networks, respectively. Local address–A local address is any address that appears on the inside portion of the network.
Global address–A global address is any address that appears on the outside portion of the network.
QUESTION 187
Refer to the exhibit. A company wants to use NAT in the network shown.
Which commands will apply the NAT configuration to the proper interfaces? (Choose two.) 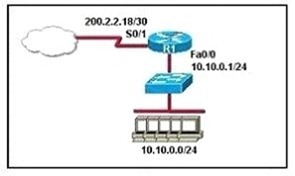
A. R1(config)# interface serial0/1
R1(config-if)# ip nat inside
B. R1(config)# interface serial0/1
R1(config-if)# ip nat outside
C. R1(config)# interface fastethernet0/0
R1(config-if)# ip nat inside
D. R1(config)# interface fastethernet0/0
R1(config-if)# ip nat outside
E. R1(config)# interface serial0/1
R1(config-if)# ip nat outside source pool 200.2.2.18 255.255.255.252
F. R1(config)# interface fastethernet0/0
R1(config-if)# ip nat inside source 10.10.0.0 255.255.255.0
Answer: BC
QUESTION 188
Which of the following statements are TRUE regarding Cisco access lists? (Choose two.)
A. In an inbound access list, packets are filtered as they enter an interface.
B. In an inbound access list, packets are filtered before they exit an interface.
C. Extended access lists are used to filter protocol-specific packets.
D. You must specify a deny statement at the end of each access list to filter unwanted traffic.
E. When a line is added to an existing access list, it is inserted at the beginning of the access list.
Answer: AC
Explanation:
In an inbound access list, packets are filtered as they enter an interface. Extended access lists are used to filter protocol specific packets. Access lists can be used in a variety of situations when the router needs to be given guidelines for decision-making. These situations include:
Filtering traffic as it passes through the router
To control access to the VTY lines (Telnet)
To identify “interesting” traffic to invoke Demand Dial Routing (DDR) calls
To filter and control routing updates from one router to another There are two types of access lists, standard and extended. Standard access lists are applied as close to the destination as possible (outbound), and can only base their filtering criteria on the source IP address. The number used while creating an access list specifies the type of access list created. The range used for standard access lists is 1 to 99 and 1300 to 1999. Extended access lists are applied as close to the source as possible (inbound), and can base their filtering criteria on the source or destination IP address, or on the specific protocol being used. The range used for extended access lists is 100 to 199 and 2000 to 2699.
Other features of access lists include:
Inbound access lists are processed before the packet is routed. Outbound access lists are processed after the packet has been routed to an exit interface. An “implicit deny” is at the bottom of every access list, which means that if a packet has not matched any preceding access list condition, it will be filtered (dropped). Access lists require at least one permit statement, or all packets will be filtered (dropped). One access list may be configured per direction for each Layer 3 protocol configured on an interface The option stating that in an inbound access list, packets are filtered before they exit an interface is incorrect.
Packets are filtered as they exit an interface when using an outbound access list. The option stating that a deny statement must be specified at the end of each access list in order to filter unwanted traffic is incorrect. There is an implicit deny at the bottom of every access list.
When a line is added to an existing access list, it is not inserted at the beginning of the access list. It is inserted at the end. This should be taken into consideration. For example, given the following access list, executing the command access-list 110 deny tcp 192.168.5.0 0.0.0.255 any eq www would have NO effect on the packets being filtered because it would be inserted at the end of the list, AFTER the line that allows all traffic.
access-list 110 permit ip host 192.168.5.1 any
access-list 110 deny icmp 192.168.5.0 0.0.0.255 any echo
access-list 110 permit any any
QUESTION 189
From which of the following attacks can Message Authentication Code (MAC) shield your network?
A. DoS
B. DDoS
C. spoofing
D. SYN floods
Answer: C
Explanation:
Message Authentication Code (MAC) can shield your network from spoofing attacks. Spoofing, also known as masquerading, is a popular trick in which an attacker intercepts a network packet, replaces the source address of the packets header with the address of the authorized host, and reinserts fake information which is sent to the receiver. This type of attack involves modifying packet contents. MAC can prevent this type of attack and ensure data integrity by ensuring that no data has changed. MAC also protects against frequency analysis, sequence manipulation, and ciphertext-only attacks. MAC is a secure message digest that requires a secret key shared by the sender and receiver, making it impossible for sniffers to change both the data and the MAC as the receiver can detect the changes.
A denial-of-service (DoS) attack floods the target system with unwanted requests, causing the loss of service to users. One form of this attack generates a flood of packets requesting a TCP connection with the target, tying up all resources and making the target unable to service other requests. MAC does not prevent DoS attacks. Stateful packet filtering is the most common defense against a DoS attack.
A Distributed Denial of Service attack (DDoS) occurs when multiple systems are used to flood the network and tax the resources of the target system. Various intrusion detection systems, utilizing stateful packet filtering, can protect against DDoS attacks. In a SYN flood attack, the attacker floods the target with spoofed IP packets and causes it to either freeze or crash. A SYN flood attack is a type of denial of service attack that exploits the buffers of a device that accept incoming connections and therefore cannot be prevented by MAC. Common defenses against a SYN flood attack include filtering, reducing the SYN-RECEIVED timer, and implementing SYN cache or SYN cookies.
QUESTION 190
Refer to the exhibit. After the power-on-self test (POST), the system LED of a Cisco 2950 switch turns amber. What is the status of the switch? 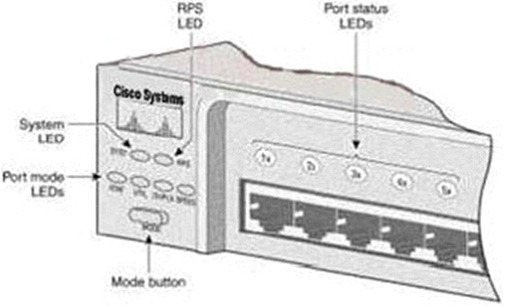
A. The POST was successful.
B. The switch has a problem with the internal power supply and needs an external power supply to be attached.
C. POST failed and there is a problem that prevents the operating system from being loaded.
D. The switch has experienced an internal problem but data can still be forwarded at a slower rate.
E. The switch passed POST, but all the switch ports are busy.
Answer: C
Explanation:
http://www.cisco.com/en/US/products/hw/switches/ps607/products_tech_note09186a00801 25913.shtml
Each time you power up the switch, eight Power-On Self Tests (POSTs) run automatically. POSTs check the most important system components before the switch begins to forward packets. When the switch begins the POST, the port status LEDs display amber for two seconds, and then display green. As each test runs, the port status LEDs go out. 1x is the first to go out. The port status LEDs for ports 2x through 8x go out sequentially as the system completes a test.
When the POST completes successfully, the port status LEDs go out. This indicates that the switch is operational. If a test fails, the port status LED associated with the test displays amber. The system LED also displays amber.
NotE. From Cisco IOS Software Release 11.2(8.5) SA6 onwards, the port and system LEDs both remain amber after a POST failure. In the earlier Cisco IOS Software Releases, only the LEDs of failed linked ports remained amber.
Latest 100-105 questions and answers from Cisco Exam Center offered by Lead2pass for free share now! Read and remember all real questions answers, Guarantee pass 100-105 real test 100% or full money back!
100-105 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDWUdDVE1SbVBrb1k
2016 Cisco 100-105 exam dumps (All 274 Q&As) from Lead2pass:
http://www.lead2pass.com/100-105.html [100% Exam Pass Guaranteed]