2016 November Cisco Official New Released 350-018 Dumps in Lead2pass.com!
100% Free Download! 100% Pass Guaranteed!
350-018 easy pass guide: Preparing for Cisco 350-018 exam is really a tough task to accomplish. However, Lead2pass delivers the most comprehensive braindumps, covering each and every aspect of 350-018 exam curriculum.
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/350-018.html
QUESTION 859
Which two statements about DTLS are true?(Choose two.)
A. If DPD is enabled.DTLS can fall back to a TLS connection.
B. It is disabled by default if you enable SSL VPN on the interface.
C. It uses two simultaneous IPSec tunnels to carry traffic.
D. If DTLS is disabled on an interface, then SSL VPN connections must use SSL/TLS tunnels.
E. Because if requires two tunnels, it may experience more latency issues than SSL connections.
Answer: AC
QUESTION 860
What protocol does SMTPS use to secure SMTP connections?
A. TLS
B. AES
C. Telnet
D. SSH
Answer: A
QUESTION 861
What security element must an organization have in place befor it can implement a security audit and validate the audit results?
A. a security policy
B. an Incident Response Team
C. Network access control
D. Firewalls
E. a Security Operations Center
Answer: A
QUESTION 862
Which two router configurations block packets with the type 0 routing header on the interface?(Choose two) 
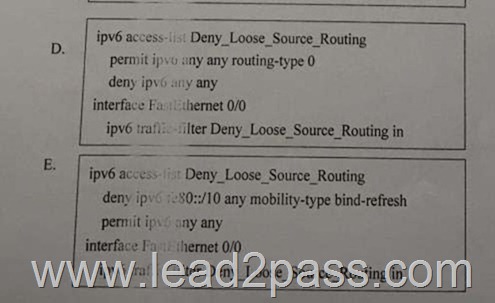
A. A
B. B
C. C
D. D
E. E
Answer: BC
QUESTION 863
What are three ways you can enforce a BCP38 policy on an Internet edge device? (Choose three.)
A. Avoid RFC 1918 internal addressing.
B. Apply ingress filters for RFC 1918 addresses
C. Apply ingress ACL. Filters for BOGON routes
D. Implement source NAT
E. Implement Unicast RPF.
F. Implement Cisco Express Forwarding.
Answer: BCE
QUESTION 864
Refer to the exhibit. What feature must be implemented on the network to produce the given output? 
A. CAR
B. NBAR
C. WFQ
D. PQ
E. CQ
Answer: B
QUESTION 865
What is an example of a WEP cracking attack?
A. Cafe Latte attack
B. Reflected XSS attack
C. Directory traversal attack
D. SQL injection attack
Answer: A
QUESTION 866
Which statement about remote procedure calls is true?
A. They can be invoked by the client and the server
B. They can emulate different hardware specifications on a single platform
C. They support synchronous and asynchronous requests
D. They use a special assembly instruction set to process remote code without conflicting with other remote processes
E. They support optimized data replication among multiple machines
Answer: D
QUESTION 867
Refer to the exhibit. Routers R1,R2, and R3 have IPv6 reachability, and R1 and R3 are able to ping each other with IPv6 global unicast address. However, R1 and R3 are unable to ping eachother with their link-local address.
What is a possible reason for the problem? 
A. Multicast must be enabled to allow link-local address to traverse multiple hops.
B. Link-local addresses can be used only with a physical interface’s local network
C. ICMPv6 packets are dropped when the destination uses a link-local address
D. Link-local addresses are forwarded by IPv6 routers using loopback interfaces
E. Link-local address can communicate with neighboring nodes only if routing is enabled between them
Answer: B
QUESTION 868
Refer to the exhibit. Which effect of this configuration is true? 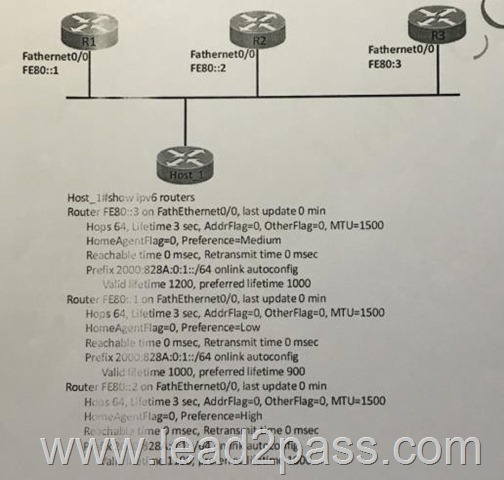
A. Host_1 learns about R1, R2 and R3 and prefers R2 as its default router.
B. Host_1 learns about R2, R3 only and R3 and prefers R3 as its default router.
C. Host_1 selects R2 as its default router and load balances between R2 and R3
D. Host_1 learns about R1, R2 and R3 and load balances between them.
E. Host_1 learns about R2, R3 only and R3 and prefers R2 as its default router.
Answer: A
QUESTION 869
Refer to the exhibit. What type of attack is illustrated? 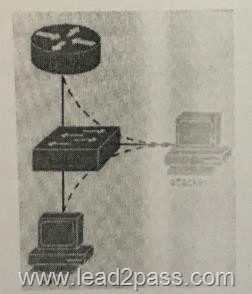
A. IP address spoofing
B. ICMP flood
C. CAM overflow
D. ARP spoofing
Answer: D
QUESTION 870
Refer to the exhibit. Which command caused the above messages? 
A. neighbor 101.0.0.1 maximun-prefix 500 70 warning-only
B. neighbor 101.0.0.1 maximun-prefix 500 70
C. neighbor 101.0.0.1 maximun-prefix 500 80 warning-only
D. neighbor 101.0.0.1 maximun-prefix 500 90
Answer: B
QUESTION 871
Refer to the exhibit. What is the effect of the given service policy configuration? 
A. It blocks Facebook.com, msn.com, cisco.com, and google.com, and permits all other domains.
B. It blocks all domains except cisco.com, msn.com, cisco.Facebook.com
C. It blocks all domains except Facebook.com, msn.com, cisco.com, and google.com
D. It blocks cisco.com, msn.com, and Facebook.com and permits all other domains
Answer: B
QUESTION 872
What is the maximum pattern length supported by FPM searches within a packet?
A. 1500 bytes
B. 256 bytes
C. 512 bytes
D. 128 bytes
Answer: B
QUESTION 873
For which reason would an RSA key pair need to be removed?
A. PKI architecture would never allow the RSA key pair removal
B. The existing CA is replaced and the new CA requires newly generated keys
C. The CA is under DoS attack
D. The CA has Suffered a power outage
Answer: B
QUESTION 874
Which statement about the cisco AnyConnect Web Secruity module is true?
A. It is deployed on points to route HTTP traffic to ScanSafe.
B. It is VPN client software that works over the SSL protocol.
C. It is an endpoint component that is used with smart tunnels in a Clientless
D. It operates as an NAC Agent when it is configured with the AnyConnect VPN client
Answer: B
QUESTION 875
Which two statement about ICMP redirect messages are true? (Choose two)
A. Redirects are only to the CPU if the packets are also source-routed
B. By default, configuring HSRP on the interface disables ICMP redirect functionality
C. They are generated by the host to inform the router of an alternate route to the destination
D. They are generated when a packet enters and exits the same router interface
E. The messages contain an ICMP Type 3 and ICMP code 7
Answer: BD
QUESTION 876
Refer to the exhibit. If you apply the given command to a Cisco device running IOS or IOS XE, which two statements about connections to the HTTP server on the device are true? (Choose two) 
A. Connections will close after 60 seconds or as soon as the first request is processed
B. When you apply the command. The device will immediately close any existing connections that have been open for longer than 90 seconds
C. The device will close each connection after 90seconds even if a connection is actively processing a request
D. Connections will close after 60 seconds without activity or 90 seconds with activety
E. Connections will close after 60 seconds without activity or as soon as the first request is processed
Answer: CD
QUESTION 877
Which two options are differences between automation and orchestration? (Choose two)
A. Orchestration is focused on an end to-end process or workflow
B. Automation is a f workflow composed of tasks. And orchestration is a technical task
C. Automation is focused on automating a single or multiple tasks
D. Automation is to be used to replace human intervention
E. Orchestration is focused on multiple technologies to be integrated together
Answer: AC
QUESTION 878
Refer to the exhibit.
SW1#config t
SW1(config)#dot1x system-auth-control
SW1(config)#exit
Which statement about the effect of this configuration is true?
A. It blocks all EAPOL from passing through the switch
B. It puts all ports on the switch into the authorized state
C. It enables 802.1x globally on the switch
D. It disables the of guest VLANs on the switch
Answer: C
QUESTION 879
Which Cisco product solution is designed for workload mobility between public-public and Private-public clouds?
A. Cisco metapod
B. Cisco Intercloudfubric
C. Cisco Unified Cloud
D. Cisco Cloud Orthestrator
Answer: B
Lead2pass provides guarantee of Cisco 350-018 exam because Lead2pass is an authenticated IT certifications site. The 350-018 dump is updated with regular basis and the answers are rechecked of every exam. Good luck in your exam.
350-018 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU2RpRGdWY3E1NEU
2016 Cisco 350-018 exam dumps (All 894 Q&As) from Lead2pass:
http://www.lead2pass.com/350-018.html [100% Exam Pass Guaranteed]